
Privileged Access Management Solutions Market By Component (Software, Service), By Deployment Mode (On-Premises, Cloud), By End-Use Industry,(BFSI, IT & Telecommunication, Other), By Region And Companies - Industry Segment Outlook, Market Assessment, Competition Scenario, Trends, And Forecast 2023-2032
-
39430
-
July 2023
-
179
-
-
This report was compiled by Vishwa Gaul Vishwa is an experienced market research and consulting professional with over 8 years of expertise in the ICT industry, contributing to over 700 reports across telecommunications, software, hardware, and digital solutions. Correspondence Team Lead- ICT Linkedin | Detailed Market research Methodology Our methodology involves a mix of primary research, including interviews with leading mental health experts, and secondary research from reputable medical journals and databases. View Detailed Methodology Page
-
Quick Navigation
Report Overview
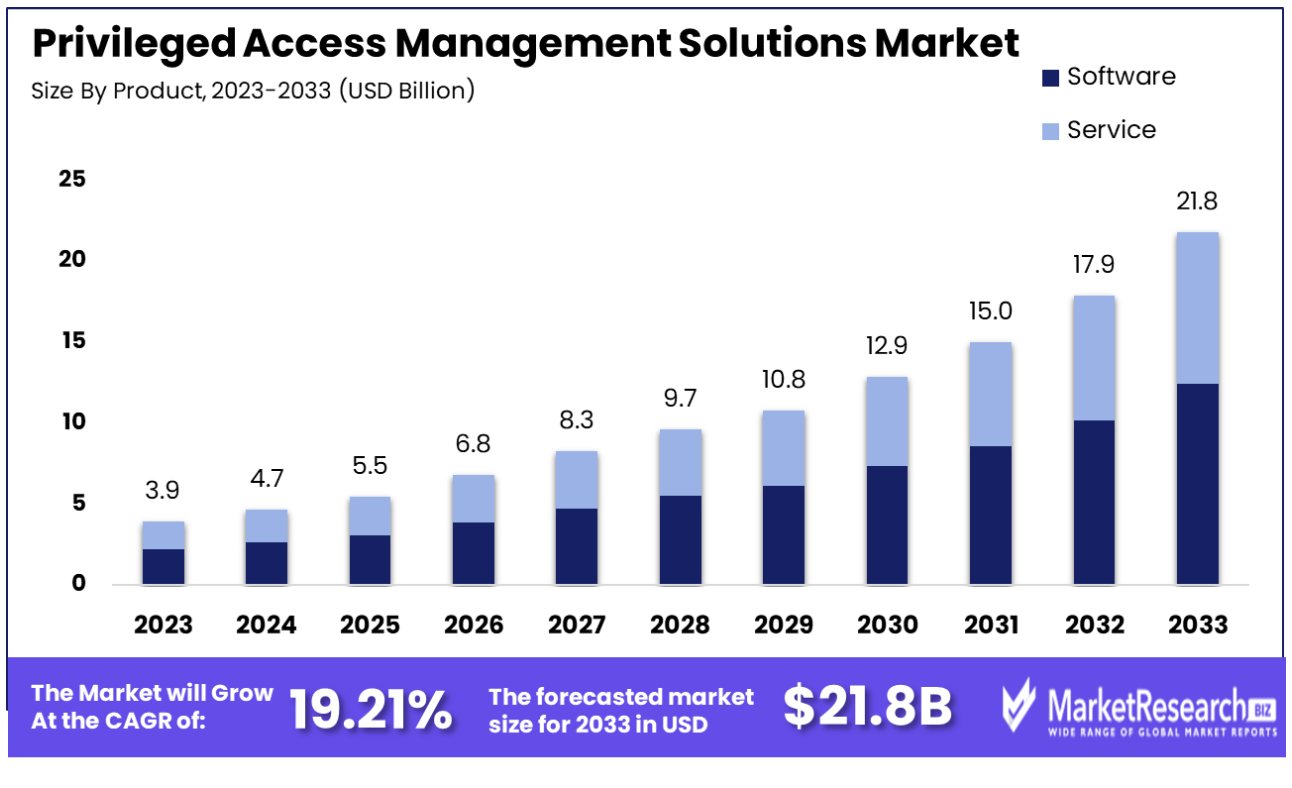
The privileged access management market was valued at USD 3.93 billion in 2023. It is expected to reach USD 25.73 billion by 2033, with a CAGR of 19.21% during the forecast period from 2024 to 2033.
The surge in demand for multi-cloud and hybrid technology, as well as the rise in cybersecurity threats, are some of the main driving factors for the privileged access management market. Privileged access management is the integration of equipment and advanced technologies that are used to safeguard, control, and supervise access to a company’s important data and resources.
The main goal of privileged access management solutions is to improve security by reducing the risk of privileged accounts being accessed, used, or taken advantage of by people who shouldn't be able to. These solutions reach this high goal by putting in place strong authentication, permission, and auditing systems. This makes it easier to follow industry rules and strengthens defenses against both outside and inside threats.
The ability to centralize and simplify the difficult task of handling privileged accounts is a key benefit of the privileged access management solutions market. Organizations can use the power of privileged access management solutions to automate these tasks rather than depending on time-consuming manual processes and cumbersome spreadsheets to track and monitor privileged access. By doing this, administrative costs are cut down, accuracy is improved, and there is consistency in how privileged access is managed across the company.
As we move deeper into the realm of important innovations, the privileged access management solutions market has seen great advancements in areas like biometric authentication, machine learning algorithms for anomaly detection, and seamless integration with other cutting-edge cyber security tools. By confirming the name of users before granting them privileged account access, the realm of biometric authentication, with fingerprint or facial recognition as prime examples, adds an extra layer of security.
Machine learning algorithms allow organizations to find and stop potential security threats before they happen by making it possible to spot unusual or suspicious trends of behavior. This, in turn, lets security problems be fixed quickly and decisively when they start. By correlating privileged access data with other security events and alerts and integrating it with other strong cybersecurity tools like security information and event management (SIEM) systems, privileged access management solutions improve the overall security of organizations.
Leading technology companies are investing a lot in privileged access management solutions, which shows how important they are becoming. Smart cybersecurity companies have built privileged access management features right into their current products, which shows how important these solutions are for protecting digital infrastructures.
Driving factors
More Cyber Threats and Data Breaches
Today's digital ecosystem has more cyber threats and data breaches. Hackers and malevolent actors can exploit vulnerabilities and steal sensitive data due to our interconnected lives, businesses, and devices. Organizations of all sizes and industries must protect against cyber threats and safeguard data.
The privileged access management solutions market reduces cyber threats and data breaches. Businesses are realizing the importance of strong privileged access security to secure key assets and prevent illegal access. Using privileged access management solutions, organizations may impose rigorous access rules, monitor privileged user activity, and detect suspicious or abnormal behavior that may suggest a breach.
Growing Adoption of Cloud Computing and Virtualization Technologies
Cloud computing and virtualization technologies have changed how businesses work and store data. Scalability, adaptability, and cost-efficiency have accelerated the adoption of these technologies across industries. However, multi-tenant cloud infrastructures increase the risk of illegal access and data breaches.
Data Protection Regulations are Strict
With data privacy at the forefront, regulatory compliance requirements have tightened. Governments and industry authorities around the world have acknowledged the need for enhanced data protection measures to safeguard the privacy and confidentiality of personal and commercial data. Failure to follow these rules can lead to financial, reputational, and legal consequences.
Rising Awareness of the Importance of Privileged Access Security
As cyber threats change and become more sophisticated, businesses and individuals are realizing the importance of privileged access security. A data breach or illegal access can cause financial loss, reputational damage, and legal liabilities. Thus, organizations are investing more in security, including privileged access management solutions.
Identity and Access Management Solutions are Required
The growing requirement for enhanced identity and access management solutions spurred the privileged access management solutions market. In today's complex and dynamic business environments, traditional approaches to identity and access management are often insufficient. The importance of securing and managing privileged access grows as organizations adopt new technologies, accept remote work, and communicate across scattered teams.
Restraining Factors
Complex Implementation and Integration
Today's digital world requires privileged access management solutions. These solutions control privileged account access to secure sensitive data and reduce data breaches. Despite their importance, organizations often confront various restraining obstacles when implementing and integrating the privileged access management solutions market.
Lack of Competent Professionals to Manage Privileged Access Solutions
Another restraining aspect is the lack of experienced professionals who possess the expertise to manage privileged access solutions. As demand for these solutions grows, organizations often struggle to locate experts to handle the implementation, setup, and continuing management of privileged access management systems.
By Component Analysis
The software segment dominates the privileged access management (PAM) solutions market. Businesses across industries are using PAM software to manage privileged access due to the growing demand for robust security measures. Organizations may secure their vital systems and data with the help of the software segment's extensive feature set and functionalities.
PAM software adoption in emerging economies depends on economic growth. Businesses are becoming more aware of the necessity for strong security measures to protect their sensitive information as these economies experience significant expansion. The software segment provides tools and technologies to secure system access and prevent illegal activity.
Consumer behavior regarding PAM software is also positive. With more high-profile data breaches and cyber-attacks, individuals and businesses are realizing the importance of privileged access management. They want software solutions with security and usability.
By Deployment Mode Analysis
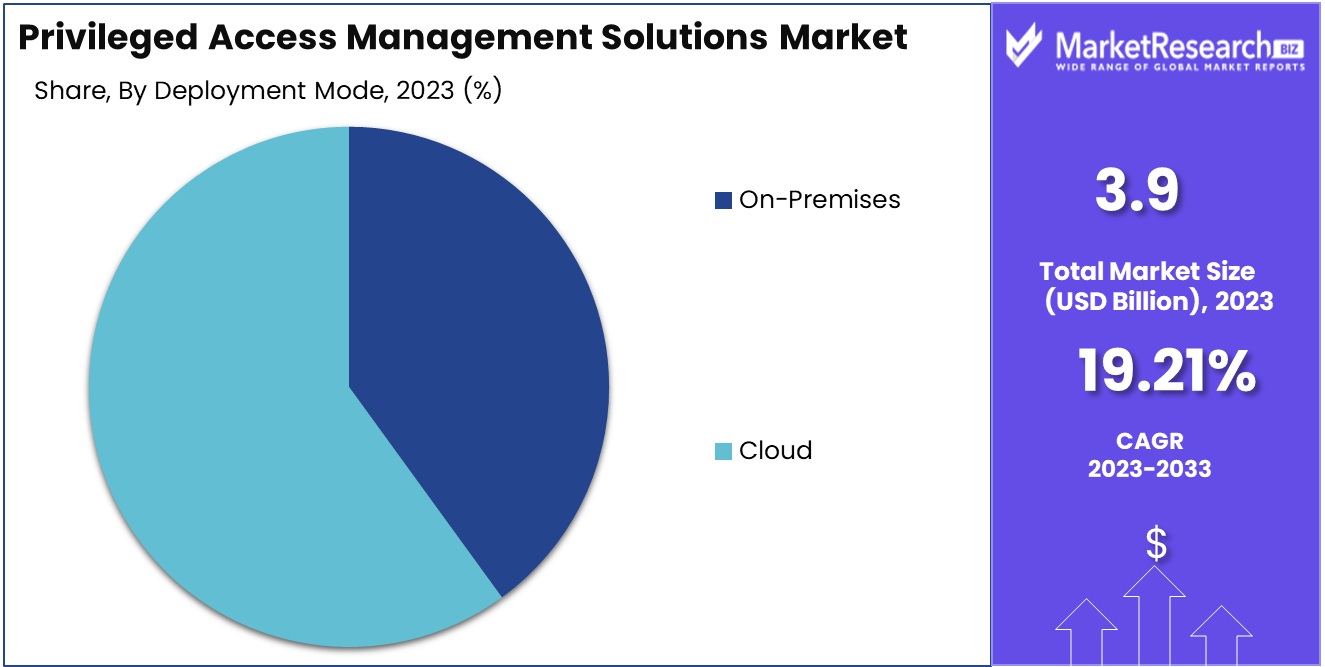
Privileged Access Management (PAM) solutions are dominated by cloud deployment. Cloud-based PAM solutions offer flexibility, scalability, and cost-effectiveness. To simplify their privileged access management procedures, businesses of all sizes and industries are adopting the cloud deployment paradigm.
Emerging economies are driving cloud-based PAM solutions adoption. As businesses in these economies flourish, demand for secure data access grows. Cloud deployment meets their increasing security needs with scalability and affordability.
Consumer attitudes and behavior regarding cloud-based PAM solutions are favorable. Businesses are discovering the benefits of cloud implementation, including lower infrastructure costs, simplified management, and increased access. They want cloud solutions with strong security and flexibility.
In the next years, the cloud segment of the privileged access management solutions market is expected to register the quickest growth rate. Several things can be attributed to this. First, the scalability of cloud-based solutions lets businesses seamlessly expand their privileged access management capabilities as their demands develop. In a continually evolving technology context, this scalability is essential.
By End-Use Industry Analysis
Privileged Access Management (PAM) solutions are dominated by the BFSI (Banking, Financial Services, and Insurance) sector. This industry needs strong security due to the digitization of financial services and the potential of cyberattacks. PAM solutions protect BFSI systems and data with complete security features.
Emerging economies are driving BFSI PAM solutions adoption. These economies' financial services sectors are growing rapidly, necessitating stronger security. PAM solutions help BFSI organizations control privileged access and prevent unwanted actions.
The BFSI consumer trend and behavior toward PAM solutions is encouraging. Businesses and individuals in the BFSI industry are becoming increasingly aware of the need for privileged access management as a result of the complexity of financial transactions and the developing threat landscape. They want security solutions that match regulations.
BFSI is expected to register the fastest growth in the privileged access management solutions market. Several things can be attributed to this. First, the BFSI industry handles massive volumes of sensitive data, making it a cyber-attack target. PAM solutions provide organizations with tools and technologies to secure their key systems and prevent unwanted access.
Key Market Segments
By Component
- Software
- Service
By Deployment Mode
- On-Premises
- Cloud
By End-Use Industry
- BFSI
- IT & Telecommunication
- Government Sector
- Healthcare
- Energy and Utilities
- Other End-Use Industries
Growth Opportunity
Privileged Access Management Demand Rising
Demand for comprehensive security solutions is rising in the privileged access management solutions market. Organizations are realizing the importance of successfully managing and controlling access to sensitive data and vital systems as cyber-attacks become more sophisticated. Thus, the demand for privileged access management solutions has increased.
Comprehensive Solutions Drive Privileged Access Management Market
A comprehensive privileged access management solutions market includes privileged password management, session monitoring, access request and approval workflows, and privileged session management. Organizations can improve security and restrict access to important resources by employing a comprehensive solution. Providers in the market have a great opportunity to develop thanks to the rising demand for comprehensive privileged access management solutions.
AI-Powered Threat Detection Grows Privileged Access Management Market
Organizations may improve their threat detection and response capabilities by implementing AI and machine learning capabilities into the privileged access management solutions market. This connection helps organizations detect illegal access, insider risks, and data breaches. The market demand for privileged access management solutions with advanced threat detection technology is promising.
Latest Trends
Changing PAM Solutions Improve Cybersecurity
In the rapidly evolving digital landscape of the present day, organizations confront numerous challenges in securing their sensitive data and essential resources. As the sophistication of cyber threats continues to increase, traditional security measures are no longer adequate to protect against unauthorized access and data intrusions. This has resulted in the emergence of the privileged access management (PAM) solutions market as a crucial element of comprehensive cybersecurity strategies.
Reinventing Privilege Access Management with Zero Trust
The shift toward Zero Trust security models is one of the main market trends reshaping the landscape of the privileged access management solutions market. Zero Trust takes a more proactive approach to safeguarding privileged accounts than conventional network security models, which rely on perimeter-based defenses.
Multifactor Authentication & Biometrics Strengthening Access Security
Multifactor authentication (MFA) and biometric verification are increasingly incorporated into privileged access management strategies across industries. MFA increases security by requiring users to provide multiple forms of authentication, such as passwords, tokens, smart cards, or biometric factors such as fingerprints or facial recognition.
Regional Analysis
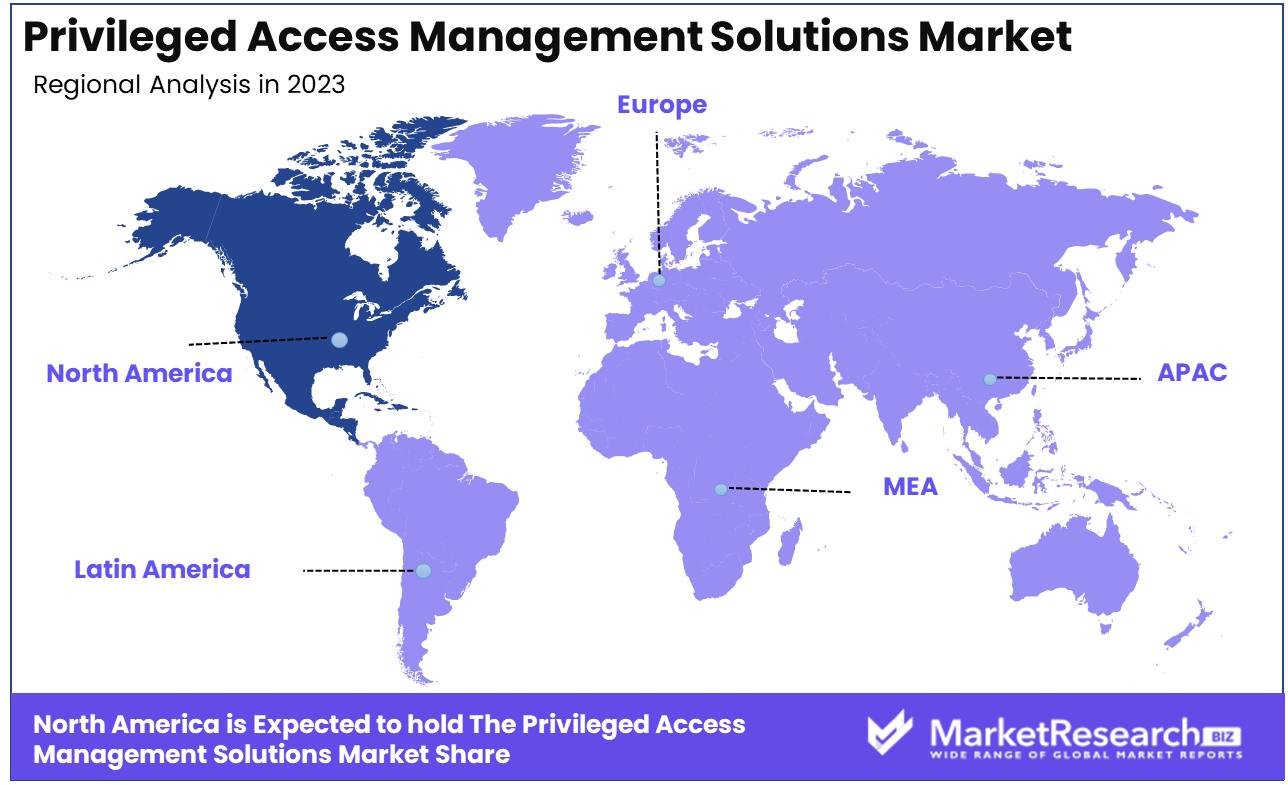
Privileged Access Management Solutions Market Dominates in North America Region. Businesses are focusing more on security in the digital age, where cyber attacks are getting more complex and ubiquitous. Privilege access management (PAM) solutions assist organizations protect their most sensitive data by managing and regulating user access to privileged accounts.
Recent years have seen rapid growth in the privileged access management solutions market. With a 10.3% compound annual growth rate (CAGR), it is projected to reach $7.6 billion by 2027. PAM solutions are being adopted by organizations in banking, healthcare, IT and telecommunications, government, and others, driving this growth.
North America dominates the PAM market. Several variables explain this region's competitive edge. First, North America is home to some of the world's biggest technology and financial companies, requiring stronger security.
Key Regions and Countries
North America
- US
- Canada
- Mexico
Western Europe
- Germany
- France
- The UK
- Spain
- Italy
- Portugal
- Ireland
- Austria
- Switzerland
- Benelux
- Nordic
- Rest of Western Europe
Eastern Europe
- Russia
- Poland
- The Czech Republic
- Greece
- Rest of Eastern Europe
APAC
- China
- Japan
- South Korea
- India
- Australia & New Zealand
- Indonesia
- Malaysia
- Philippines
- Singapore
- Thailand
- Vietnam
- Rest of APAC
Latin America
- Brazil
- Colombia
- Chile
- Argentina
- Costa Rica
- Rest of Latin America
Middle East & Africa
- Algeria
- Egypt
- Israel
- Kuwait
- Nigeria
- Saudi Arabia
- South Africa
- Turkey
- United Arab Emirates
- Rest of MEA
Key Players Analysis
The privileged access management solutions market is dominated by key players such as BeyondTrust Corporation, Centrify Corporation, CyberArk Software Ltd, SecureAuth Corporation, One Identity LLC, and Zoho Corporation Pvt Ltd. Each of these companies brings its own expertise and technologies to the table, providing organizations with robust and comprehensive solutions to combat the escalating cyber threats.
Centrify Corporation provides a unified infrastructure for privileged access management, combining identity and access management (IAM) and privileged access management (PAM) capabilities. Centrify provides organizations with a comprehensive and scalable security solution by integrating privileged access controls into IAM in a seamless manner. Their solutions integrate comprehensive multi-factor authentication capabilities with privileged identity management, privileged session management, and privileged password management.
Top Key Players in Privileged Access Management Solutions Market
- BeyondTrust Corporation.
- Centrify Corporation.
- CyberArk Software Ltd.
- SecureAuth Corporation.
- One Identity LLC
- Zoho Corporation Pvt Ltd.
- Ekran System
- Simeio Solutions
Recent Development
- In 2022, ThycoticCentrify, a renowned name in the cyber security industry, introduced its new Privileged Access Management (PAM) system, ThycoticCentrify Privilege Cloud.
- In 2021, IBM Security's acquisition of Resilient Systems, a prominent provider of security orchestration automation and response (SOAR) solutions, made headlines.
- In 2020, ForeScout Technologies, a prominent player in the PAM industry, finalized its acquisition of Perspecsys.
- In 2019, The renowned identity and access management (IAM) provider Okta acquired the prominent IAM market player Auth0.
Report Scope:
Report Features Description Market Value (2022) USD 2.75 Bn Forecast Revenue (2032) USD 28.5 Bn CAGR (2023-2032) 24.40% Base Year for Estimation 2022 Historic Period 2016-2022 Forecast Period 2023-2032 Report Coverage Revenue Forecast, Market Dynamics, COVID-19 Impact, Competitive Landscape, Recent Developments Segments Covered By Component (Software, Service), By Deployment Mode (On-Premises, Cloud), By End-Use Industry,(BFSI, IT and telecommunication, Government Sector, Healthcare, Energy and Utilities, Other End-Use Industries) Regional Analysis North America – The US, Canada, & Mexico; Western Europe – Germany, France, The UK, Spain, Italy, Portugal, Ireland, Austria, Switzerland, Benelux, Nordic, & Rest of Western Europe; Eastern Europe – Russia, Poland, The Czech Republic, Greece, & Rest of Eastern Europe; APAC – China, Japan, South Korea, India, Australia & New Zealand, Indonesia, Malaysia, Philippines, Singapore, Thailand, Vietnam, & Rest of APAC; Latin America – Brazil, Colombia, Chile, Argentina, Costa Rica, & Rest of Latin America; Middle East & Africa – Algeria, Egypt, Israel, Kuwait, Nigeria, Saudi Arabia, South Africa, Turkey, United Arab Emirates, & Rest of MEA Competitive Landscape BeyondTrust Corporation., Centrify Corporation., CyberArk Software Ltd., SecureAuth Corporation., One Identity LLC, Zoho Corporation Pvt Ltd., Ekran System, Simeio Solutions Customization Scope Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements. Purchase Options We have three licenses to opt for: Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited User and Printable PDF) -
-
- BeyondTrust Corporation.
- Centrify Corporation.
- CyberArk Software Ltd.
- SecureAuth Corporation.
- One Identity LLC
- Zoho Corporation Pvt Ltd.
- Ekran System
- Simeio Solutions




